Our Risk Assessment Process
Understand Your Security Position With a Cyber Security Risk Assessment
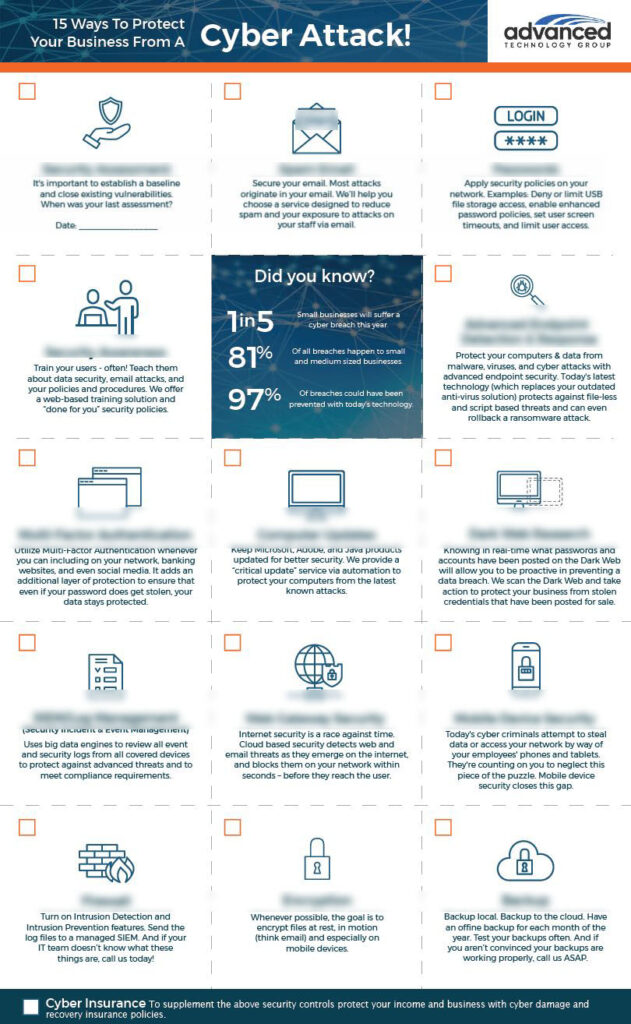
In today’s complex security landscape, it’s impossible to prevent all threats. Just like your insurance policy, security is all about managing your risks. With a cyber security risk posture assessment, we can evaluate and mitigate risky activities that leave you vulnerable to a cyber attack and potential disruption of your operations.
A Holistic View of Your Security Health
Our approach to security starts with a global view of your security health. Like a 100-point inspection on your car, we take a proactive assessment of your policies, procedures, and technology to assess security gaps and their level of severity. Together, we’ll discuss the gaps found, why they matter, and how to address each risk.
Backed by a Trusted Cybersecurity Framework
While there are many approaches to cybersecurity, we believe in standardizing on an industry-wide framework. Our risk assessment is based on the NIST Cybersecurity Framework, developed and backed by the U.S. government. This framework enables us to apply the best practices of risk management across your entire organization to improve our ability to prevent, detect, and respond to cyberthreats.
Allocate Your Security Budget Wisely
We know you have a limited budget to allocate to IT and security measures, and we want you to spend it wisely. We’ll show you which gaps, if left unaddressed, would cause the greatest financial and operational impact. This allows us to determine where your budget can be most impactful.
A Road-map to Mitigate Your Top Risks
By performing a risk assessment, you gain a clearer picture of what vulnerabilities your business is exposed to, putting you in a position to respond effectively, and cost-efficiently, when working towards closing those detected security gaps.
Here are the 5-Steps we will perform:
| 1) ASSESS | 2) ANALYZE | 3) DEVELOP A ROAD MAP | 4) EXECUTE | 5) RE-ASSESS |
|---|---|---|---|---|
| Schedule time to assess risk (call or in person) | Evaluate the results and determine your current risk posture | Review risks and create an action plan to address each risk | Implement the action plan on agreed upon timetable | Re-evaluate risk posture in 6-12 months |